Risk management in engineering

Risk management is an inherent and very often invisible and intangible part of everything we do. Every day we make decisions, sometimes without thinking too much about it, and some decisions require more thinking because of uncertainty. This is where risk management brings value - it helps to navigate these uncertainties. For example, you are starting a new high-profile engineering initiative, and you want to have a good level of confidence that decisions you take during this initiative are not going to jeopardise its delivery.
Let’s see how it works in practice!
Below you can see a classic end-to-end risk management process.
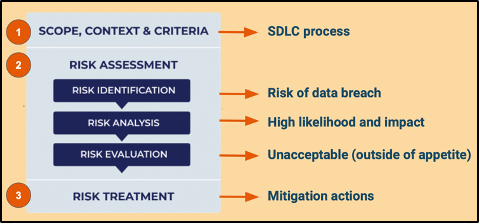
Step 1: scope, context & criteria
To begin with, we start with identifying scope, context and criteria. For
example, given the context of your engineering initiative, you want to
focus on the Software Delivery Lifecycle (SDLC) part of it as it is the
most uncertain. You also determined that, as your criteria, you are not
going to accept any high risks.
Step 2: risk assessment
Next step includes risk assessment, which is broken down in risk identification, analysis and evaluation:
- Risk identification can be accomplished through brainstorming, historical data analysis and expert judgment and some of the most common risks you can identify in the context of SDLC is a risk of data breach.
- As you identify your risk, you proceed with analysis of its likelihood and impact. Using helpful risk management tools such as risk matrix, you identified that the risk of data breach is of high likelihood and high impact.
- Then you evaluate your risk and determine if it is acceptable or not, or how we say in risk management if it is within or outside of appetite. Given the fact that during step 1 you identified that you are not going to accept any high risks, your data breach risk is outside appetite.
Then, we proceed with selecting and implementing appropriate risk treatment option. In my experience, the most common treatment option for engineering risks, especially those that are not acceptable, is mitigation, which means implementing measures to reduce risk. For our risk of data breach, these can include implementation of multifactor authentication, review of password policies and encryption of data.
As the above steps are conducted, it is important to remember to engage with internal and external stakeholders who are involved in your initiative. This one sounds like common sense, but I have seen on numerous occasions how lack of stakeholder engagement can lead to delayed or even failing initiatives. For example, focusing too much on the technical aspects of the initiatives and not liaising with the compliance colleagues, can lead to a technically fit initiative, but not compliant with data protection requirements making it impossible to deploy it to your clients. Also remember to continually monitor and review the risks and mitigating actions and document the outcomes and report to stakeholders.
If you commit to following the above steps, you can control areas of uncertainty associated with your initiative and enable your team to succeed and meet your organisational objectives.
Additional resources:
To learn more about risk management, there are plenty of standards and best practices, which I highly recommend getting familiar with. Some of them include:
- ISO 31000: Risk Management framework is an international standard that provides organisations with guidelines and principles for risk management.
- ISO/IEC 27001: Information security management.
- OWASP Guidelines: Best practices for web application security.
- IEEE Standards: Guidelines for software project management and quality assurance
